STORAGE PROTECTION Technology

01
What is Storage Protection Technology?
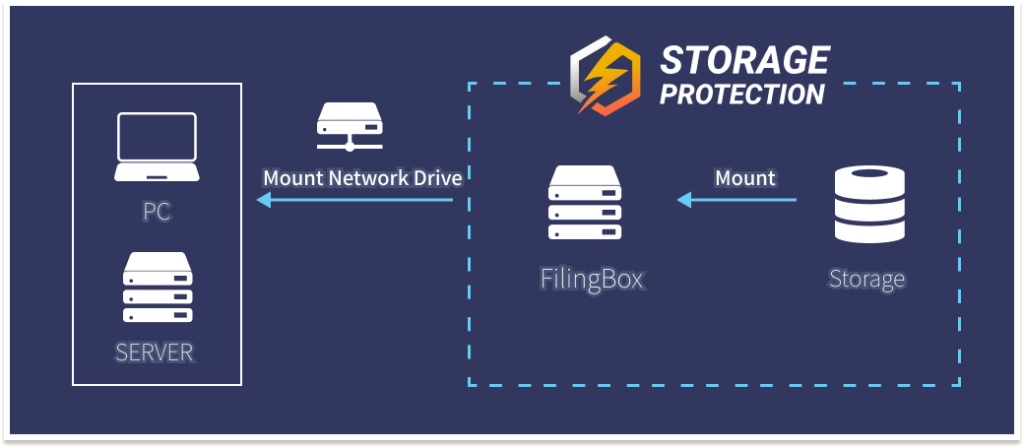
Storage protection technology protects data in a network drive against ransomware and data breach malware attacks while using data. It allows preregistered applications to read, modify, and delete data in a network drive, but others don’t. It works like a firewall in the middle of PC and storage. It is effective and efficient to protect data compared to any other protection technology because it already knows what application will use what data. This is a technology protecting data from a network storage standpoint for ransomware and data breach malware prevention.
02
Why is it secure?
But,If you use storage protection technology together with your conventional storage, you can protect your data from unknown latest ransomware and data breach malware.
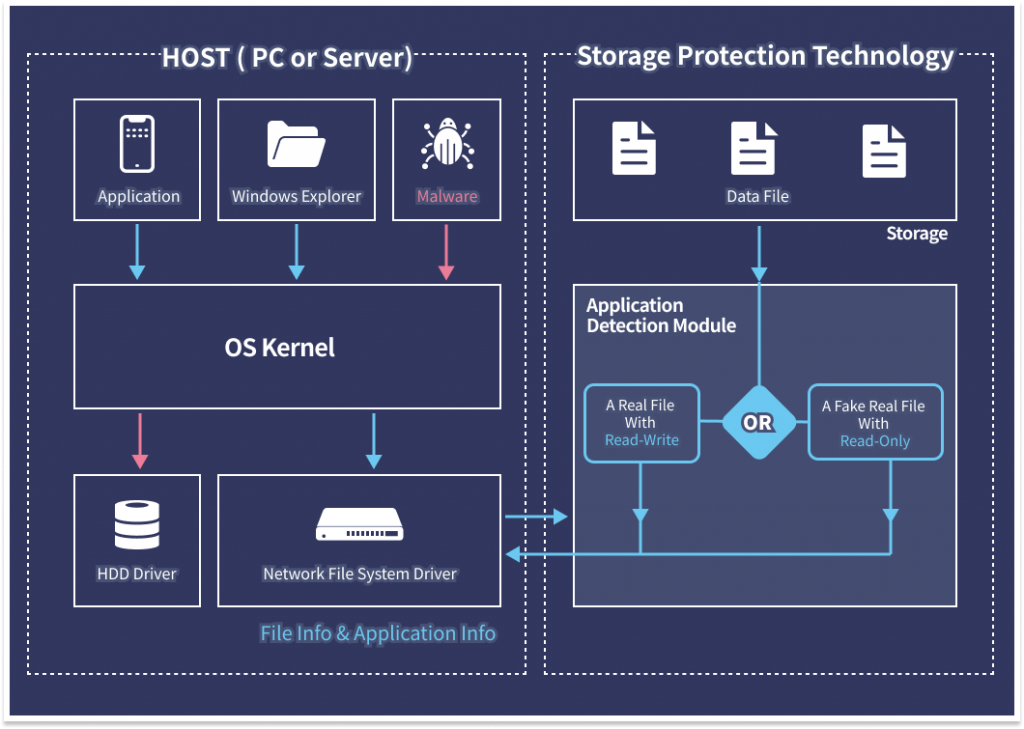
Conventional storage only knows what data is being requested,but doesnt know what application is asking for the data. But storage protection technology adds the application detection module to the storage and provides data to only the preregistered application after examining the application requesting data.
So,it protects your data securely from latest unknown ransomware and data breach malware while preregistered applications can use data safely.
The reason that we chose a network storage structure separated from PCs is it can protect data on the network storage because the protection mechanism runs in network storage outside of PCs, even though ransomware and data breach malware is already running on PCs. Furthermore, malware cannot attack the network storage through a network drive interface because a network drive is already a part of the OS. If so, the OS is stopped and the malware is also dead.
03
Why is it called storage protection technology?
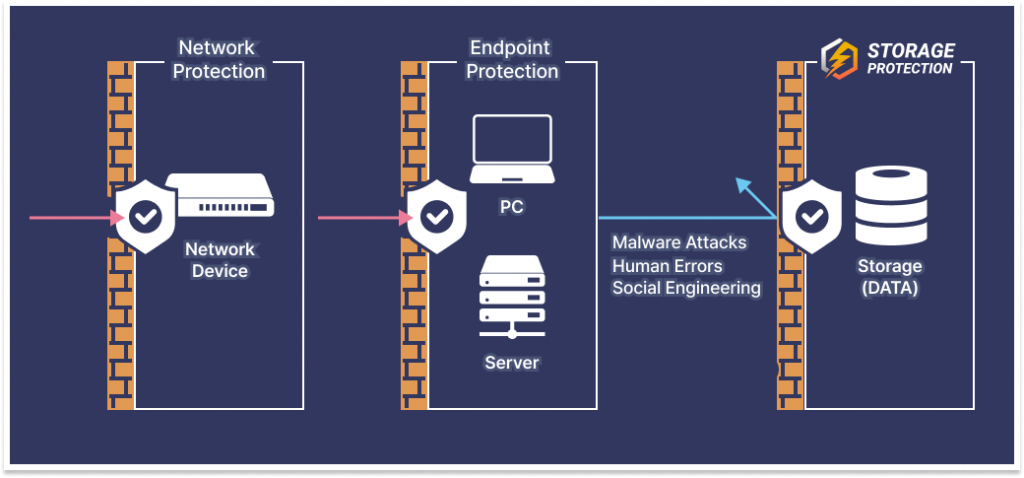
As network protection and endpoint protection technology have a detection module on the network and endpoint device, we added a detection module to the storage, which allows only preregistered applications to read, modify, and delete data on the storage. In addition, it works well with existing network protection and endpoint protection solutions because the working area is different. The emphasize is on the importance of adding one more protection layer to the storage, like network protection and endpoint protection technology does.
04
How was it developed?
So, there needs to be a way to protect a file from data breach malware. Initially, we developed a file system that blocked the provision of a file to unregistered applications. But it created problems in Anti-virus vaccines and other applications which continued to ask for a file until opened. It made the PC slow because it kept asking for a file until the PC’s computing power was maximum.
So, the protection method was changed to provide a fake file to unregistered applications. It didn’t generate any problems for an application that could generate a file request infinitely, but the vulnerability of data breach malware attacks could be overcome.



05
Why does the storage protection technology keep upgrading?
Initially, a fake file system was developed that worked at the application level. It became FilingBox MEGA, which allows only registered applications to read, write, modify, and delete data.
Then, a fake file system that worked at the drive level was also created. It became FilingBox Team, which allows only a manager to switch all files as fake files on the network drive at once. It is very useful to protect your files from data breach malware in a small group.
Lastly, a fake file system that worked at the file level was developed. It is called FilingBox SMB, which allows only a user with a higher user security level compared to a security level of a file to read a real file. This is a good use case demonstrating how storage protection technology can be coupled with document access security for enhancing internal document security.
We keep finding new ways to enhance document protection and security without losing convenience. Keep watching our future developments.
06
Hybrid WORM Network Storage Demo

